Bluetooth is one of the most ubiquitous wireless technologies in the world found in phones, laptops, cars, smart home devices, wearables, and even medical devices. Its convenience is unmatched, but so are its security risks. As Bluetooth adoption grows, so does the attack surface. Hackers, security researchers, and penetration testers use specialized tools to audit and exploit Bluetooth vulnerabilities.
In this blog, we explore the Top 5 Bluetooth Hacking Gadgets in 2026 what they are, how they work, why they matter, and most importantly, how you can protect yourself or your organization from threats involving them.
⚠️ Important Note Before We Begin
This blog is for educational purposes only — highlighting security tools so you can understand risks and defenses. Misusing hacking tools without permission is illegal and unethical. Always conduct security testing with explicit authorization.
📌 What Is Bluetooth Hacking?
Bluetooth hacking refers to exploiting weaknesses in Bluetooth protocols or implementations to gain unauthorized access, intercept communications, spoof devices, or execute malicious actions.
Common Bluetooth attack types include:
- Eavesdropping — capturing data transmitted between devices
- Bluejacking — sending unsolicited messages
- Bluesnarfing — accessing data without authorization
- Bluetooth Low Energy (BLE) spoofing — impersonating trusted devices
- Man-in-the-Middle (MITM) attacks
The gadgets and tools below help security professionals discover, audit, and exploit these vulnerabilities.
🧰 Top 5 Bluetooth Hacking Gadgets in 2026
1️⃣ Ubertooth One

📌 Overview
The Ubertooth One is one of the most famous Bluetooth security research platforms. It’s an open-source development board designed to monitor and interact with Bluetooth traffic, including Classic Bluetooth and Bluetooth Low Energy (BLE).
It was developed by Great Scott Gadgets and has become a staple in wireless security research.
🔍 What It Can Do
- Passive Bluetooth monitoring — sniff Bluetooth packets
- Bluetooth Classic & BLE analysis
- Spectrum analysis (limited)
- Packet capture for offline analysis
- Works with tools like Wireshark
🎯 Key Features
| Feature | Description |
|---|---|
| Open-Source | Community driven, firmware can be modified |
| Affordable | ~$120 USD |
| Compatible | Works on Linux, macOS, Windows |
| Extensible | Supports custom firmware and tools |
📈 Use Cases
✔ Discover nearby Bluetooth devices
✔ Audit device communications
✔ Capture BLE advertising packets
✔ Analyze pairing mechanisms
⚠️ Limitations
- Does not break Bluetooth encryption by itself
- Range limited compared to specialized SDRs
- Requires technical knowledge
💡 Who It’s For
Security researchers, penetration testers, and RF enthusiasts who need a compact, affordable Bluetooth monitoring platform.
2️⃣ Proxmark3 RDV4

📌 Overview
The Proxmark3 is primarily known as a radio frequency (RF) research and RFID/NFC hacking tool, but its latest RDV4 hardware can be extended to support wide RF ranges — including Bluetooth frequencies (2.4 GHz) with the right firmware and antennas.
While not designed exclusively for Bluetooth, Proxmark3’s flexibility makes it a powerful platform for Bluetooth security research.
🔍 What It Can Do
- RFID/NFC security research
- RF signal capture and replay
- Bluetooth packet capture (with proper setup)
- Hardware-level device interaction
🎯 Key Features
- Powerful FPGA + MCU architecture
- Large community and open-source firmware
- Extensible with multiple antennas
💡 Why It’s Relevant for Bluetooth
With third-party firmware and custom front-ends, researchers have experimented with Bluetooth and BLE signals — especially for capturing advertising packets or identifying devices.
⚠️ Limitations
- Not plug-and-play for Bluetooth
- Requires hardware knowledge
- Limited Bluetooth support compared to Ubertooth
3️⃣ HackRF One

📌 Overview
The HackRF One is a software-defined radio (SDR) capable of transmitting and receiving over a very wide frequency range (1 MHz – 6 GHz). That includes Bluetooth frequencies around 2.4 GHz.
SDRs like HackRF are extremely powerful for wireless research — but also require deep technical expertise.
🔍 What It Can Do
- Capture Bluetooth and BLE signals
- Transmit custom RF packets
- Perform spectrum analysis
- Work with tools like GNU Radio and Universal Radio Hacker (URH)
🎯 Key Features
| Feature | Description |
|---|---|
| Wide Frequency Range | Covers all Bluetooth bands |
| Open-Source Tools | GNU Radio, URH, GQRX |
| Transmit & Receive | Not just passive monitoring |
📈 Use Cases
✔ Reverse-engineer Bluetooth protocols
✔ Build custom Bluetooth sniffers
✔ Explore RF spectrum interference
✔ Test jamming and spoofing scenarios
⚠️ Limitations
- Requires significant technical expertise
- Can be powerful enough to violate local regulations (transmission requires compliance)
- Not focused solely on Bluetooth
4️⃣ Bluefruit LE Sniffer (Adafruit)


📌 Overview
The Bluefruit LE Sniffer from Adafruit is a dedicated Bluetooth Low Energy packet sniffer. It’s designed for developers and security testers to capture BLE traffic and analyze communication between BLE devices.
Unlike Ubertooth, it focuses solely on BLE traffic.
🔍 What It Can Do
- Capture BLE advertising and connected traffic
- Integrates with Wireshark
- Works with Nordic Semiconductor chips (nRF51822)
🎯 Key Features
- Affordable (~$20–$30 USD)
- Plug-and-play with Wireshark
- Ideal for BLE protocol analysis
📈 Use Cases
✔ Debug BLE device communication
✔ Identify BLE services & characteristics
✔ Capture pairing attempts
✔ Security testing BLE peripherals
⚠️ Limitations
- BLE only — no Classic Bluetooth
- Passive only — cannot inject or transmit
- Limited range
5️⃣ Bluetooth Firmware Modded Devices (e.g., nRF Dev Boards)
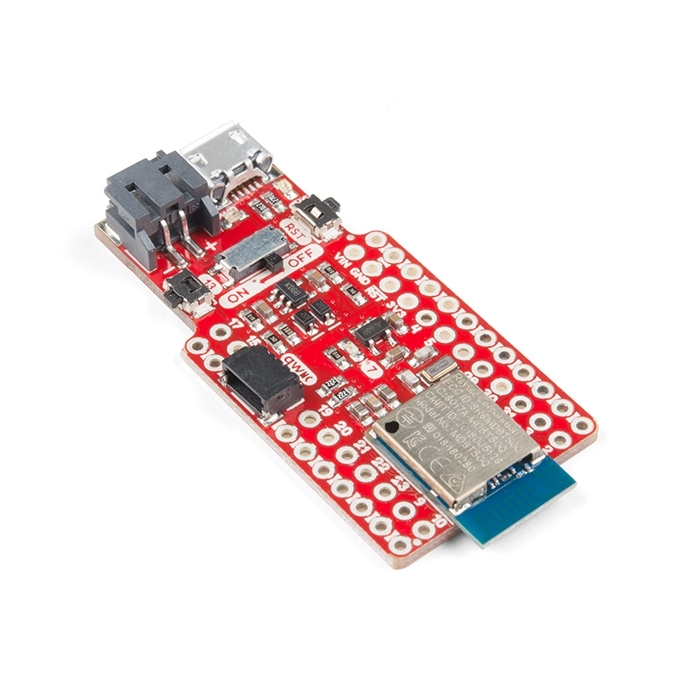
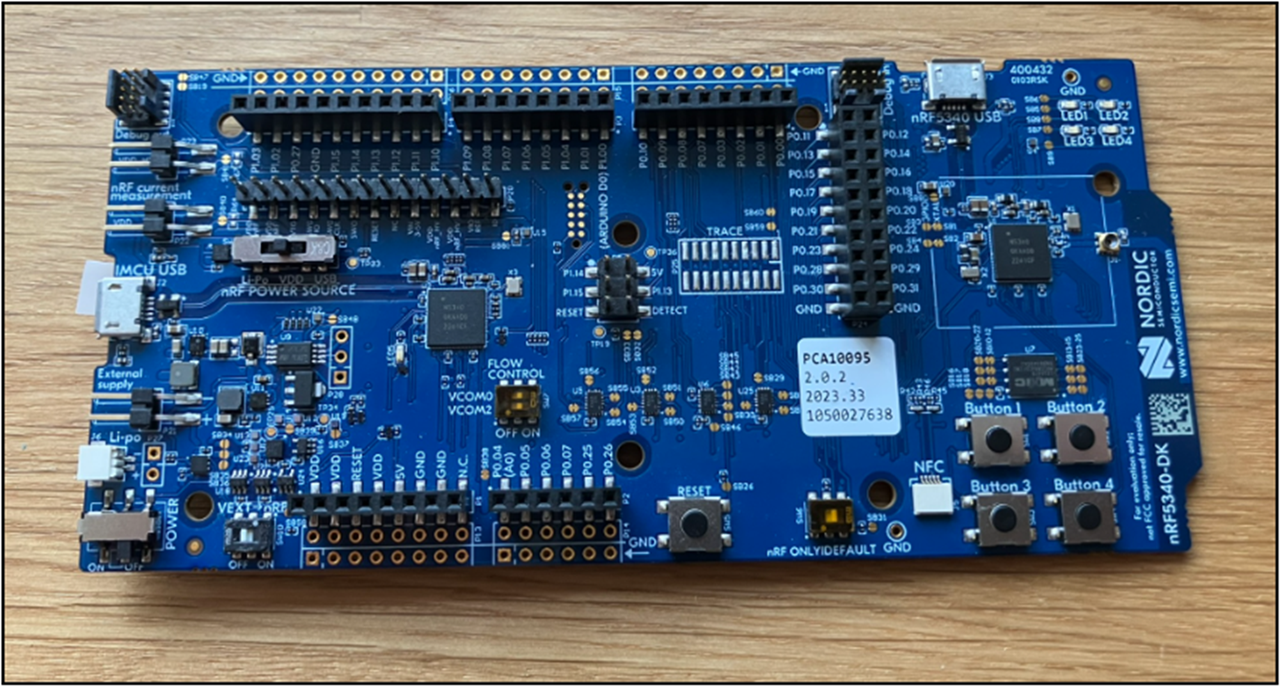


📌 Overview
Not a single off-the-shelf gadget — but programmable Bluetooth development boards (like Nordic nRF52 series) are among the most versatile tools available. With custom firmware, these boards can act as:
- BLE scanners
- Packet injectors
- Fake peripherals
- Pairing attackers
🔍 What They Can Do
- Advertise fake BLE services
- Spoof trusted devices
- Perform BLE fuzzing
- Run automated attacks
🎯 Key Features
| Feature | Description |
|---|---|
| Programmable | Customize behavior via firmware |
| BLE & Bluetooth Support | Depending on chip |
| Accessible | Low cost for dev boards |
| Great for Testing | Developers can emulate devices |
📈 Use Cases
✔ Security testing BLE device pairing
✔ Teaching Bluetooth exploitation
✔ Custom RF research
✔ Bluetooth protocol fuzzing
⚠️ Limitations
- Requires firmware development skills
- Not purpose-built for hacking (need custom tooling)
📊 Comparison Table: Top Bluetooth Hacking Gadgets
| Gadget | Bluetooth Focus | Passive Sniffing | Active Attack Capability | Skill Level | Price Range (₹) |
|---|---|---|---|---|---|
| Ubertooth One | High (Classic + BLE) | Yes | Limited | Intermediate | ₹9,000–₹15,000 |
| HackRF One | Very High (Broad SDR) | Yes | Yes | Advanced | ₹13,000–₹42,000 |
| Proxmark3 RDV4 (note: generic clone) | Medium (RF flexibility) | Yes | Possible (with firmware) | Advanced | ₹11,000–₹52,000 |
| Bluefruit LE Sniffer | High (BLE-only) | Yes | No | Beginner–Intermediate | ₹2,500–₹3,000 |
| Pro Micro NRF52840 Dev Board (representing modded dev boards) | Customizable | Yes | Yes (firmware) | Intermediate–Advanced | ₹600–₹3,000+ (varies with board) |
🛡️ Ethical and Legal Considerations
Before using any of these tools, be aware:
❗ Legal Risks
- Intercepting Bluetooth traffic without consent may violate privacy laws.
- Transmitting on Bluetooth frequencies without authorization could breach radio regulations in many countries.
- Using these tools on networks/devices you don’t own or manage is illegal.
Always get written permission before performing any security testing.
🧠 How Bluetooth Hacking Happens (Simplified)
- Discovery — Identify nearby Bluetooth devices (scan)
- Sniffing — Capture packets to observe communication
- Analysis — Use tools to decode protocols or find weaknesses
- Exploitation — Inject packets, spoof devices, or break pairings
- Persistence — Maintain unauthorized presence
Bluetooth security relies on robust pairing methods like LE Secure Connections, but older devices may still use weaker pairing like “Just Works” which is vulnerable to MITM.
🧰 Essential Tools That Work with These Gadgets
| Tool | Usage |
|---|---|
| Wireshark | Analyze captured Bluetooth packets |
| GNU Radio | SDR signal processing |
| Universal Radio Hacker | RF analysis |
| BlueZ (Linux Bluetooth Stack) | Manage Bluetooth interfaces |
| Nordic SDK / nRF Connect | Develop/testing BLE firmware |
🛡️ How to Protect Against Bluetooth Attacks
Understanding attackers’ tools is half the defense. Here’s how to secure Bluetooth:
🔐 1. Use Latest Bluetooth Security Standards
- Ensure devices support BLE Secure Connections
- Avoid legacy modes
- Update firmware regularly
📶 2. Disable Bluetooth if Unused
Simple but effective — turning Bluetooth off when not needed reduces exposure.
🚫 3. Avoid Pairing in Public
Never pair in crowded or untrusted areas.
🕵️♂️ 4. Use Device Visibility Settings
- Non-discoverable mode hides devices from scans
- Limit visible time
🔄 5. Regular Firmware Updates
Manufacturers patch known vulnerabilities — update smart devices, phones, and peripherals.
🧪 6. Security Testing
Organizations should conduct regular Bluetooth vulnerability assessments using authorized testers.
📌 Real-World Bluetooth Risks
Bluetooth bugs have caused major security concerns:
- KNOB attack exploited key negotiation weaknesses
- BLESA targeted BLE pairing flaws
- Research shows car infotainment systems and medical devices vulnerable
Staying informed and patched is critical.
🧩 Bluetooth Security Checklist (Quick)
✅ Check Bluetooth version (prefer 5.x with Secure Connections)
✅ Disable discoverability
✅ Monitor paired devices regularly
✅ Update all Bluetooth devices
✅ Perform authorized security assessments
🧠 Conclusion
Top 5 Bluetooth Hacking Gadgets in 2026 , like Ubertooth One, HackRF One, and Bluefruit LE Sniffer are powerful tools used by security professionals worldwide. While the list above focuses on legitimate research and testing hardware, the same knowledge helps defenders better protect their wireless environments.
Understanding how attackers use these gadgets — and how Bluetooth protocol weaknesses are exploited — is essential for building robust wireless security strategies.
If you’re a beginner, start with Bluefruit LE Sniffer to learn BLE basics. Intermediate users can explore Ubertooth One, and advanced RF researchers will appreciate HackRF One and programmable dev boards.
Stay curious, stay ethical — and secure your Bluetooth devices!



